MoCFI: A Framework to Mitigate Control-Flow Attacks on Smartphones
tl;dr (too long; didn't read)
MoCFI is the first general control-flow integrity (CFI) framework for smartphone platforms. It protects against runtime and control-flow attacks (e.g. code injection or ROP) by enforcing that jumps go to an expected location. The implementation is on iOS though the overall technique should be applicable to Android (which also uses ARM). Note: requires jail-breaking to set an environment variable, install a shared library, and allow the library to rewrite app code during load-time.
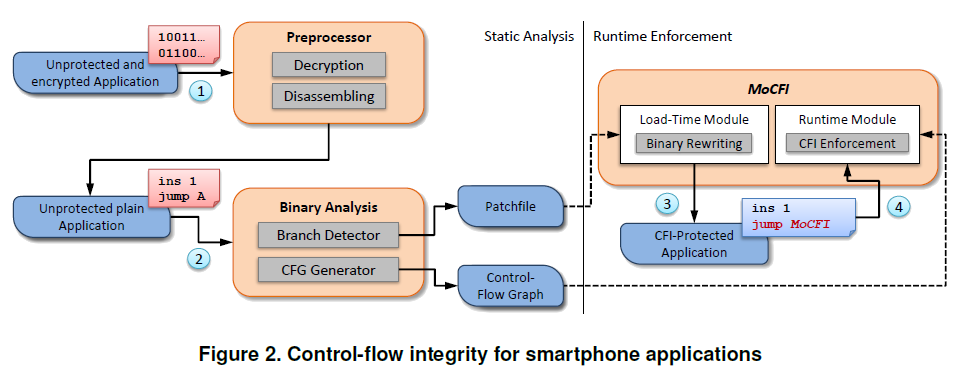
MoCFI consists of the following steps:
- IDA Pro is used to perform static analysis on an iOS app to determine branch instructions that may be exploited for a control-flow attack.
- Possible targets for each indirect branch are calculated and a Patchfile is generated that replaces these branches with trampolines to the MoCFI module.
- At load-time, a binary rewriting module applies the Patchfile to the app's image in memory. This method leaves the original app code unchanged, leaving the code signature intact.
- At run-time, each relevant branch now passes control to MoCFI which validates that the branch target resolves to one of the valid targets calculated by the static analysis step.
Abstract
Runtime and control-flow attacks (such as code injection or return-oriented programming) constitute one of the most severe threats to software programs. These attacks are prevalent and have been recently applied to smartphone applications as well, of which hundreds of thousands are downloaded by users every day. While a framework for control-flow integrity (CFI) enforcement, an approach to prohibit this kind of attacks, exists for the Intel x86 platform, there is no such a solution for smartphones.
In this paper, we present a novel framework, MoCFI (Mobile CFI), that provides a general countermeasure against control-flow attacks on smartphone platforms by enforcing CFI. We show that CFI on typical smartphone platforms powered by an ARM processor is technically involved due to architectural differences between ARM and Intel x86, as well as the specifics of smartphone OSes. Our framework performs CFI on-the-fly during runtime without requiring the application’s source code. For our reference implementation we chose Apple’s iOS, because it has been an attractive target for control-flow attacks. Nevertheless, our framework is also applicable to other ARM-based devices such as Google’s Android. Our performance evaluation demonstrates that MoCFI is efficient and does not induce notable overhead when applied to popular iOS applications.
Other Details
- Control-flow integrity (CFI) - when the control-flow of a program follows only the legitimate paths determined in advance.
- Compiler approaches won't work because source code is not available and the solutiion would be specific to a given compiler, which would not be feasible as both LLVM and GCC are widely used for iOS.
- CFI on ARM is more involved than on desktop PCs due to several architectural differences (details Section 3.3)
- The program counter is a general-purpose register
- The processor may switch the instruction set at runtime
- There are no dedicated return instructions
- Control-flow instructions may load several registers as a side-effect
- Section 2.1 and 5 have some useful info about the ARM architecture.
- Section 2.2 - Selected iOS Security Features
- W xor X (Writable xor eXecutable) memory pages since iOS v2.0
- Cannot prevent ROP attacks that leverage existing and signed code pieces.
- Stack-Smashing Protector (SSP) - canaries between local variables and control-flow info to detect stack smashing attacks.
- ASLR since iOS v4.3
- The current prototype protects an application's main code but not dynamic libraries that are loaded into the process.
- Current prototype also does not detect attacks exploiting exception handlers (when an adversary rewrites pointers to an exception handler and then deliberately causes an exception).
Diagrams
The following are relevant diagrams from the paper. Several diagrams and performance graphs have been omitted, see the paper
for details.
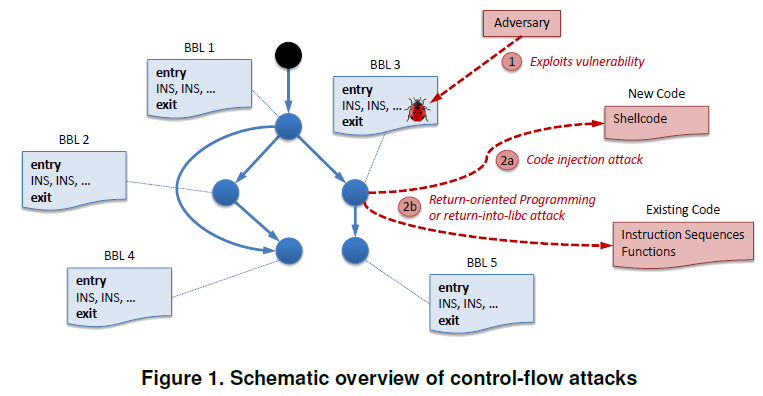
Diagram of Control Flow Attacks
MoCFI Architecture Overview
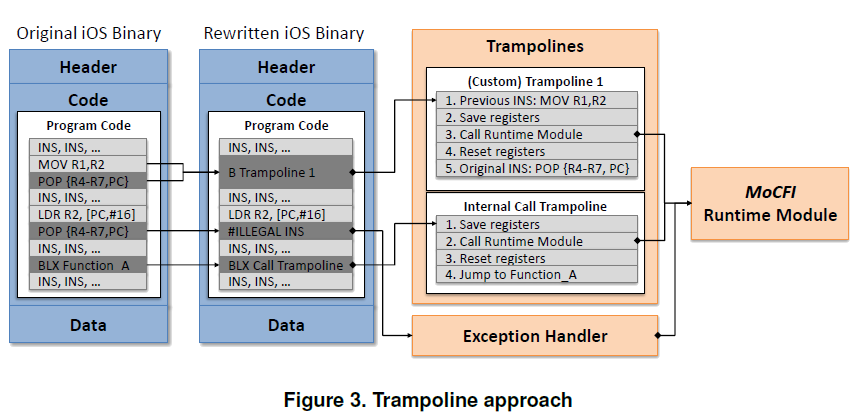
The Trampolines Inserted into Apps To Redirect Control Flow
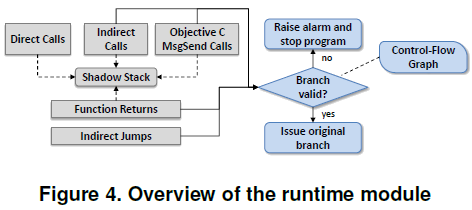
Architecture of the Run-Time Module (Branch Enforcer)
blog comments powered by Disqus